ROOM INFO
.NAME:Sublist3r .Profile: tryhackme.com Description:Learn how to find subdomains with Sublist3r!
- Task 1: Intro
As you begin this room, read the disclaimer and how the tool is been used first before proceeding, No rocket science here...lol
Lets begin:
Sublist3r is a fantastic python script that allows us to perform quick and easy recon against our target, discovering various subdomains associated with the websites/domains in scope.
Resource used:
.Sublist3r tool (github.com/aboul3la/Sublist3r)
.pip python3
- Task 2: Installation
So you are asked to install Sublist3r in the opt directory, you will need to have Python 3.4.x (or higher) or Python 2.7.x installed. We'll be using Python 3 commands. if sure you have it firstly. Now copy the Github repository for Sublist3r, you will be installing it the opt directory, The standard directory for optional package installation on any linux distro you have.
Firstly, lets change to our opt directory:
cd /opt
Cone the Sublist3r repository into opt using "git clone":
git clone https://github.com/aboul3la/Sublist3r
.Move to the Sublist3r directory, you just created:
use command to see the directory then
cd Sublist3er.
Finally, install the requirements for running Sublist3r:
pip3 install -r requirements.txt
- Task 3: Switchboard
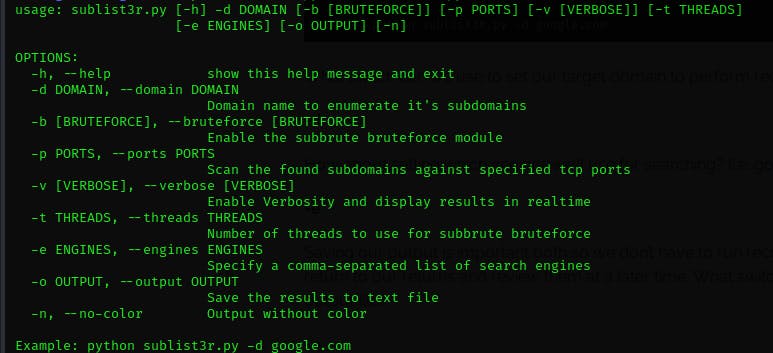
Sublist3r has a number of switches that we can use to do everything from setting our target domain to changing which engine to use for searching. You can access this via running Sublist3r with only the help switch: -h (python3 sublist3r.py -h)
 You could see an example of how it is used in a website like google.com
You could see an example of how it is used in a website like google.com
 Use the Sublist3r help command to get the switches/option
Use the Sublist3r help command to get the switches/option
- Task 4: Scans away!
Time to scan, let's run Sublit3r against a target company domain and learn about some common domains! You can also run this via the recon tool at dnsdumpster or you can also just download my results from running sublist3r.
Choose your choice but I personally would suggest go for the download if you dont know how to use dnsdumpster for recon!
Let's run sublist3r now against nbc.com, a fairly large American news company. Run this now with the command:
Run python3 sublist3r.py -d nbc.com -o sub-output-nbc.txt
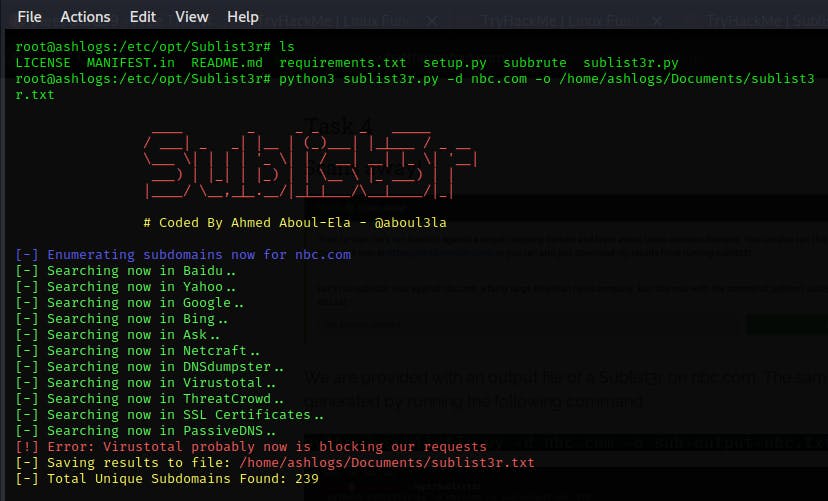
Look through the dns record results you have and pay close attention
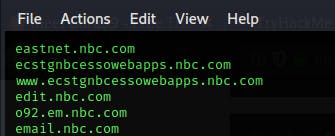
.Once that completes open up your results and take a look through them. Email domains are almost always interesting and typically have an email portal (usually Outlook) located at them. Which subdomain is likely the email portal?
mail
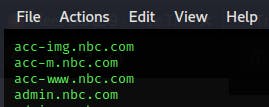
.Administrative control panels should never be exposed to the internet! Which subdomain is exposed that shouldn't be? admin
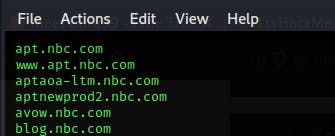
.Company blogs can sometimes reveal information about internal activities, which subdomain has the company blog at it? blog
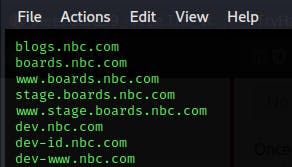
.Development sites are often vulnerable to information disclosure or full-blown attacks. Two developer sites are exposed, which one is associated directly with web development? dev-www
.Customer and employee help desk portals can often reveal internal nomenclature and other potentially sensitive information, which dns record might be a helpdesk portal? help
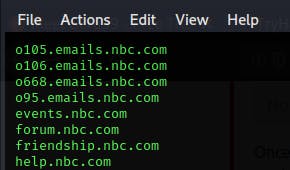
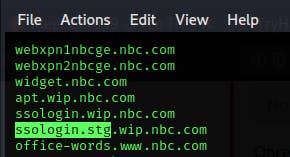
.Single sign-on is a feature commonly used in corporate domains, which dns record is directly associated with this feature? Include both parts of this subdomain separated by a period.sslologin.stg
 Lastly this needs some google dorking,
we were told "NBC produced a popular sitcom about typical office work environment"
check out what is "the office" about nbc.com in google.
Lastly this needs some google dorking,
we were told "NBC produced a popular sitcom about typical office work environment"
check out what is "the office" about nbc.com in google.
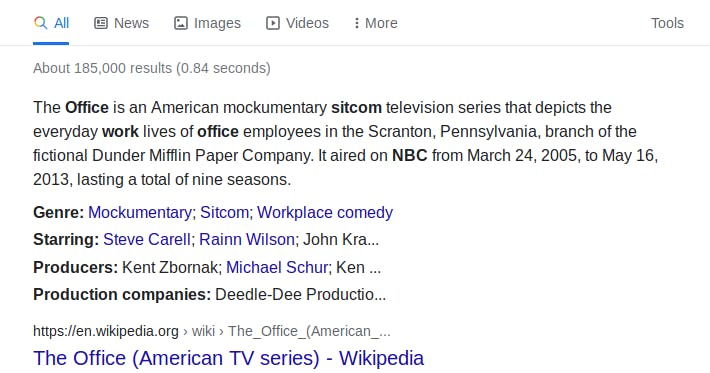
.One last one for fun. NBC produced a popular sitcom about typical office work environment, which dns record might be associated with this show? office-words
Good recon mate!!
Hope its helps someone out there...Cheers

