This room is a bit similar to the "intro 6" of the section and we are been presented with a client-code modification challenge and not spending much time on it, lets dive straight into exploiting and gaining access into the user credentials.
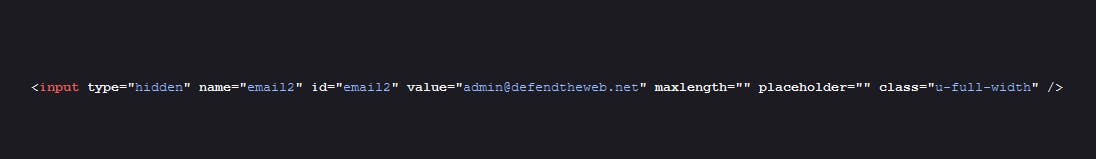
Looking into the login field, we are given the username, password and a request password section but we have no clue about the username probably we must have done a bit of ohSINT. so lets try inputting a random username and password to get a clue about the "Page source". Right-click and head to "View Page Source", looking through the codes we found a email value email2 set to the default admin email account "admin@defendtheweb.net"
but we cant interacting with the code from the page source so lets head back to the site and set the the admin account we found if we could get something fishy with the access. Cool! nothing interesting. we have to look into the "Inspect Element" from your browser to analyze and interact with the codes further.
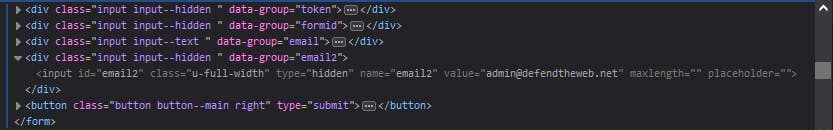
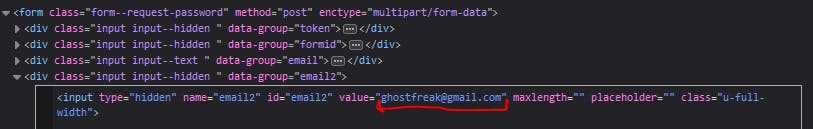
Heading straight to the Request password line of code then back to the "Inspect Element", we found the same email2 value,please pay attention to the assigned value for that specific field.
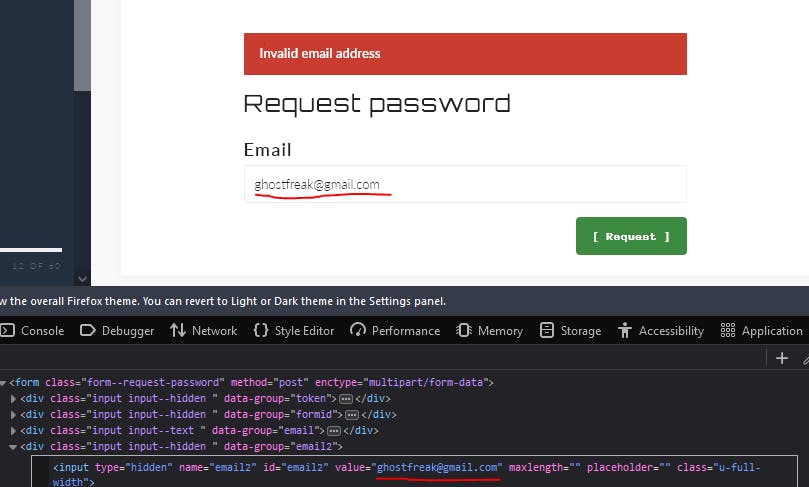
Look like the value for “email2” is set to the default admin email account “admin@defendtheweb.net.” Try editing the HTML code with your chosen random email in the the value field of the "Inspect Element" then type in the same email the field and submit the request.
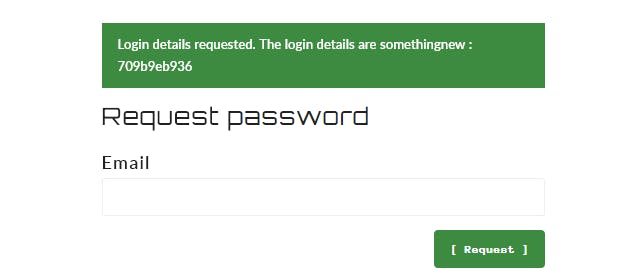
Once you submit the request, you should receive the user credentials.
Copy and paste them into the username and password field. Boom!! Pretty easy right?.
Note: Developers, This challenge just shows a tip of how your source code is a key for hackers to locate and access databases, as well as your intellectual property and using Code Access Security, ensure that your code operates in a variety of sandboxes without affecting its integrity. Validate all users and inputs. If the program works with money and important storage, user validation must have several clearances. Injection attacks will be prevented by validating data from all sources. Therefore ensure to perform a code review about your software before publishing it.