Public WI-FI can be found in almost every places like airport, malls, restaurants, coffee shops or even hostels. Which can be used by anyone either visiting or stays around its range thus used to gain access to the internet. These WI-FI are widespread and common that people frequently connect to them without asking if their connections are secure or not. Yes, Most people will say “Since its coming from a trusted source, Their connections are secured” You are absolutely right!..but think about it while business owners may believe that they are providing a valuable service to their customers, chances are the security on these network are lax and nonexistent.
Although it really sounds harmful logging into your social media accounts ,checking on news feeds or reading through your emails or even mostly checking through your bank account using this networks are chances to be RISKY.
Briefly explaining about public WI-FI, what do you think are the risk of using them.
RISKS OF USING THEM
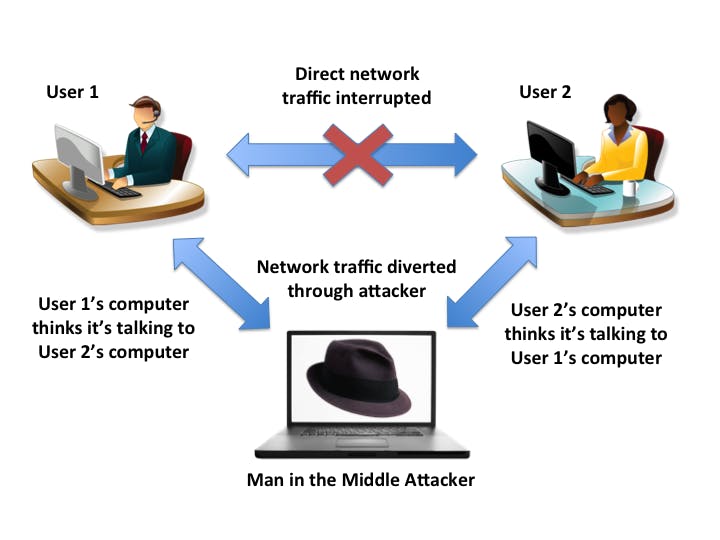
.MAN IN THE MIDDLE ATTACKS(MITM attack):
This is one of the most common threats happening in this network. If not familiar with this term..dont worry. A Man-In-The-Middle attack is when an attacker positions him/herself in an active connection between you and the Public WI-FI(tho not only for WI-FI attacks) either to impersonate one of the parties making it look like a normal active and uninterrupted connections is still undergoing.
"INSERTING THEMSELVES IN THE MIDDLE OF THE ATTACK”
So don’t believe you are secured please!!.
.Unencrypted Networks:
Encryption involves that the connection between Device A and B are private. Also means that the messages that are sent between your computer and wireless router/device are in the form of a “secret code” so that they cannot be read to anyone who doesn’t have the key to decipher the code. Wireless router encryptions mostly are by default turned off but inviting an IT pro should make it enabled.
"THERE IS NO SURE WAY TO TELL IF THIS HAS HAPPENED”

.Malicious Hotspots:
An hotspot created by cybercriminals are often used to gain access and control of victims sensitive information…wondering how they create such? Lets assume you are in a shopping mall with a name(CRYSTAL MALL) as usual their hotspot automatically on, you intend to connect to the WI-FI, there is a possibility you may think you are selecting the correct one, clicking on “CRYSTALL MALL WI-FI” but you haven’t. Instead you have gotten connected to a malicious hotspot thereby allowing the malicious hacker gain control over your sensitive information.
"TRICKING VICTIMS INTO CONNECTING TO WHAT THEY THINK IS LEGITIMATE”

.SNOOPING & SNIFFING:
WI-FI snooping and sniffing is what it sounds like(cunning & inhale) data being transmitted over a network. cybercriminals can automate certain software to assist them with eavesdropping on a WI-FI signals. This technique can allow them to access EVERYTHING that you may have doing online ,either viewing whole screen webpages you have visited to being able to capture your login credentials or even being able to hijack your accounts…sounds scarcely right?(Its not new this days).
"CAPTURING YOUR VISITED WEBPAGES AND INFO”

.Malware Distribution:
Malware is an acronym for “Malicious Software”. As the name implies, software which has been designed to operate in a harmful and undesirable manner. Security Vulnerabilities are also ways that attackers can slip malware onto your computer without your knowledge. Which are usually found in an operating system or software program. Attackers can exploit this weakness by manipulating codes to target a specific vulnerability and inject the malware onto your device.
"EVEN YOUR ANTIVIRUS MIGHT NOT SAVE YOU”
So whats the big point? AVOID THEM AT ALL COST AND BE PRIVACY CONSCIOUS.

